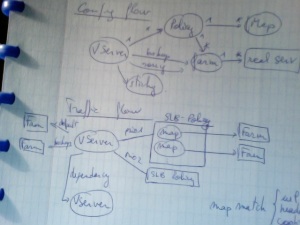
Working on security aspects for the moment. I am looking for security improvements on the datacenter network. I actually found very interesting guides. Here are some that I recommend:
Cisco IOS Security Configuration Guide, covers general security with cisco devices. It includes explanation and configuration for AAA (authentication, authorization, accounting), security servers (radius and TACACS+), filtering (ACLs, TCP intercept, CBAC, IDS), IP security (IPsec, IKE) and various advices on password, privileges levels and SSH.
Cisco Guide to Harden Cisco IOS Devices, a very comprehensive guide, which gives advices point per point, separating management, control and data planes. It goes over: AAA, logging, ACLs, securing SNMP, securing sessions (console and remote), protecting CPU, securing BGP and IGPs, anti-spoofing techniques (uRPF) and much more.
SANS Policy Primer, which gives you hints on writing a security policy.
NSA Router security configuration guide, contains good guide, but somewhat outdated.



 Posted by Arnaud Coomans
Posted by Arnaud Coomans 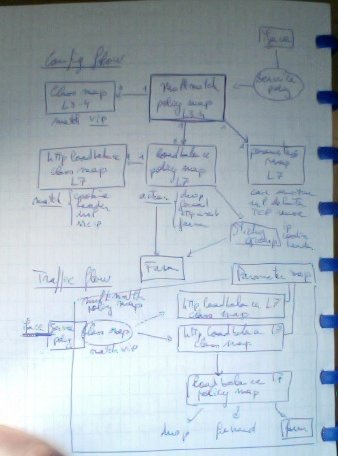
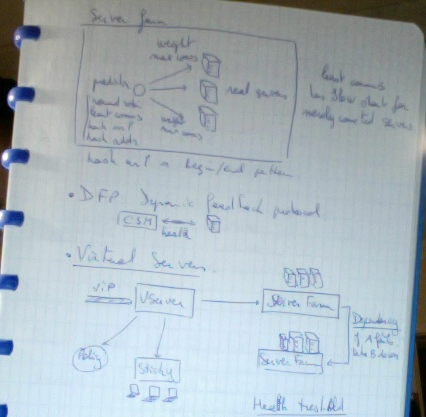 Using a predictor, that is a function, and weight for each server, denoting the share of load to put on that server, the connections are balanced on multiple servers.
Using a predictor, that is a function, and weight for each server, denoting the share of load to put on that server, the connections are balanced on multiple servers.