Working on security aspects for the moment. I am looking for security improvements on the datacenter network. I actually found very interesting guides. Here are some that I recommend:
Cisco IOS Security Configuration Guide, covers general security with cisco devices. It includes explanation and configuration for AAA (authentication, authorization, accounting), security servers (radius and TACACS+), filtering (ACLs, TCP intercept, CBAC, IDS), IP security (IPsec, IKE) and various advices on password, privileges levels and SSH.
Cisco Guide to Harden Cisco IOS Devices, a very comprehensive guide, which gives advices point per point, separating management, control and data planes. It goes over: AAA, logging, ACLs, securing SNMP, securing sessions (console and remote), protecting CPU, securing BGP and IGPs, anti-spoofing techniques (uRPF) and much more.
SANS Policy Primer, which gives you hints on writing a security policy.
NSA Router security configuration guide, contains good guide, but somewhat outdated.



 Posted by Arnaud Coomans
Posted by Arnaud Coomans 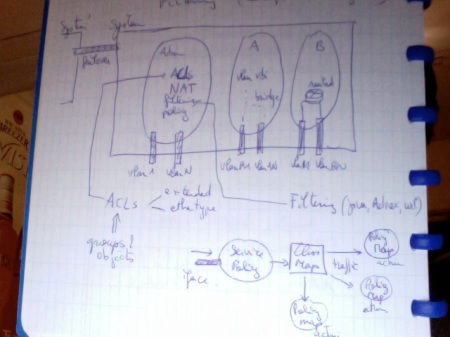
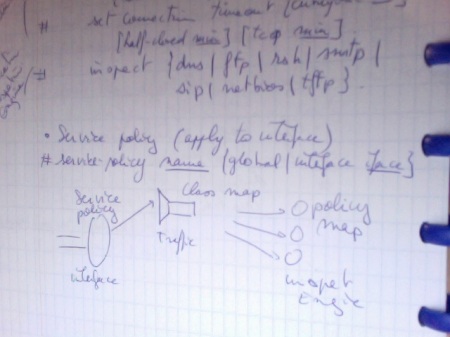 First define a service policy to be attached to an interface. Then the class map is used to select the traffic you want to filter. Finally, the policy map is used to take action: max number of connections, timeout, inspection.
First define a service policy to be attached to an interface. Then the class map is used to select the traffic you want to filter. Finally, the policy map is used to take action: max number of connections, timeout, inspection.